- Sophos Mesh Network
- Sophos Network Agent
- Sophos Network Protection
- Sophos Sg Mesh Network
- Sophos Xg Mesh Network
A Wireless Repeater is a Mesh access point which broadcasts wireless networks. That means it uses a wireless connection (the Mesh network) to connect to the Sophos Firewall, while offering other wireless connections. How to Configure a Wireless Bridge Connect the Root AP to the Sophos Firewall using an Ethernet cable.
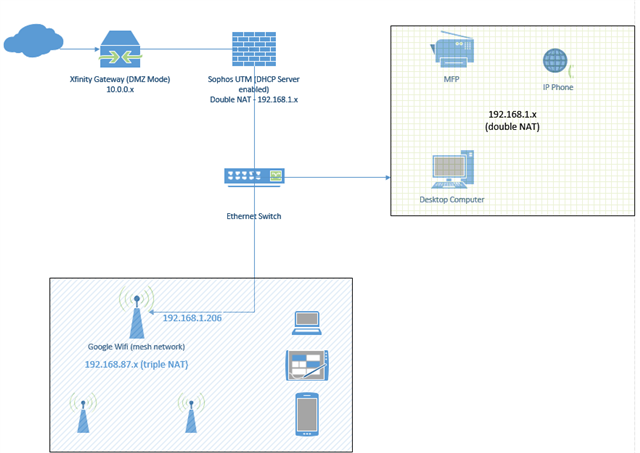
- Network topology attached. Indicators: Loss of DNS at endpoints, up2date package and DHCP client errors on UTM, Eero wireless mesh nodes offline. Isolation steps so far: I was exploring the possibility that the Eero mesh was the root cause of the problem and had replaced managed switches within the mesh network with unmanaged switches.
- A note on the internal network: If your site is small and you only need to connect 4 devices, you can patch them directly into the RED. If however you have multiple devices you can connect them to a standard switch and patch that into the RED. A personal favorite of mine is to extend the connectivity by using a Sophos Wi-Fi AP.
The internet was designed to be resilient and decentralized. Its multiple, redundant pathways between any two network nodes and its ability to accommodate new nodes on the fly should enable it to keep carrying data in the face of blocked nodes, censorship from repressive regimes or natural disasters.
However, its implementation has far diverged from its original design, with ISPs now holding the reins of the highly-centralized platform into which the internet has evolved.
Nowadays, each end user/node is stuck at the end of an isolated cul-de-sac. With the flip of ISPs’ switches, an overwhelming majority of a country’s nodes go dark.
Which is exactly what happened to protesters in Egypt when they were plunged into digital darkness after the country’s regime made some five phone calls to ISPs in the early hours of 28 January 2011.
The easily-persuaded ISPs pulled their plugs, disabling 93% of the country’s internet access within a mere 28 minutes. 22 pdf preview (e)dialectical behavioral training.
This is all detailed in a fascinating article by Julian Dibbell in the March issue of Scientific American.
In the article, Dibbell delivers an account of how Egypt’s internet shutdown was “an object lesson in the internet’s vulnerability to top-down control,” with a shutdown that was “alarmingly instructive and perhaps long overdue.”
The Egyptian cutoff is only the starkest of a growing number of examples of how vulnerable the internet has become to top-down control, writes Mr. Dibbell:
During the Tunisian revolution the month before, authorities had taken a more targeted approach, blocking only some sites from the national internet. In the Iranian post-election protests of 2009, Iran's government slowed nationwide internet traffic rather than stopping it altogether. And for years China's 'great firewall' has given the government the ability to block whatever sites it chooses. In Western democracies, consolidation of internet service providers has put a shrinking number of corporate entities in control of growing shares of internet traffic, giving companies such as Comcast and AT&T both the incentive and the power to speed traffic served by their own media partners at the expense of competitors.
In the face of an internet that can be controlled all too easily by corporations and regimes, activists are building alternative mesh networks that can never be blocked, filtered or shut down.

These networks often amount to what’s called an “internet in a suitcase”.
For example: FunkFeuer, a mesh network in greater Vienna, relies on 200 small, weatherized Wi-Fi routers on rooftops, each owned and maintained by the user who installed it, and each contributing bandwidth to a communal, high-speed internet connection throughout the city.
It costs nothing more than the $150 hardware setup, which amounts to what FunkFeuer co-founder and lead developer Aaron Kaplan refers to as “a Linksys router in a Tupperware box, basically.” Borderlands the pre sequel community patch downloadwhonew.
But can mesh networks replace the current set up?
Even committed supporters of mesh networking don’t anticipate that its promise of low-cost, do-it-yourself internet access could or should force ISPs out of the market. Jonathan Zittrain, a Harvard Law School professor and author of The Future of the Internet: And How to Stop It, told Scientific American that the centralization of ISPs has real benefits, including ease of use.
The magazine also quotes Ramon Roca, founder of Guifi.net, who doubts mesh networks could ever take much more than 15 percent of the market from the ISPs.
With that low level of penetration, however, mesh networks can serve to “sanitize the market,” Roca said, bringing the internet to low-income households and exerting downward price pressure on ISPs.
We can’t rely on market forces, nor widespread adoption due to ease of use; that makes government the next logical place to turn, Mr. Dibbell writes.
Whereas wireless mesh would serve the public good by delivering a network resistant to surveillance and censorship – things the network interprets as damage – the payoff for government would be in creating a communications channel that would route around actual damage, such as hurricanes, earthquakes or other natural disasters.
In those terms, it’s easy to imagine national security and law enforcement as being proponents of mesh.
But as Mr. Dibbell points out, it’s just as easy to imagine such entities distrusting a national mesh network, given that it’s outside the realm of surveillance and beyond earshot of the telephone and ISP companies that enable surveillance.
He writes:
Such are the complications of counting on government to support mesh networking when it is governments, often enough, that do the kind of damage mesh networks promise to help fix.
But we must bear in mind: surveillance actually does come in handy when you’re talking about cybercriminals and terrorists. As such, we could rightly wonder what the security situation might look like in a network independent of the watchful eye of ISPs and telephone companies.
As it turns out, security will likely be as do-it-yourself as the hardware, protocols, scripts and other technologies the activists are now hammering out.
For their part, those working on Eben Moglen’s FreedomBox mostly agree that it should serve as a web proxy to clean up and protect web traffic.
At this point, FreedomBox has posted a first draft of Privoxy, free software licensed under the GNU GPLv2 that serves as a non-caching web proxy with advanced filtering capabilities for enhancing privacy, modifying web page data and HTTP headers, controlling access, and removing ads and other “obnoxious internet junk.”
According to the FreedomBox site, Privoxy upgrades web traffic to prefer SSL encryption wherever possible. It also strips tracking software from web pages to provide greater privacy and anonymity to web surfers.
Future FreedomBox work will include a script to test HTTPS Everywhere rules. HTTPS Everywhere is a Firefox extension that ensures communications with a number of major websites are encrypted.
While the FunkFeuer Free Net in Vienna does maintain a list of known vulnerabilities, the group’s policy is that the onus for security lies with each node operator.
Their policy, as tweaked a bit from a kludgy translation:
The Beacon IT security team helps the beacon node owners to maintain a safe and virus/Trojan/worm-free network (and thus a well-functioning network). This is done mainly by warnings and alerts . We will not directly help individual node owners to install anti-virus protection. Downloadteamsd.
Ultimately, beacon is a 'bottom-up' power. This means that users are also responsible for the security of their router.
The IT security team reserves the right to warn, and in extreme cases, to block spammers and others who disturb the quality of the network. This should only be a last measure to protect other users or to ensure the basic function of the network.
If the idea of an internet that’s more robust in the face of surveillance and censorship appeals, now’s the time to pitch in and help projects in your country or region.
Here are a list of resources and opportunities from Scientific American:
- FreedomBox is planning future hackfests in various cities. They need help with ideas, with bug squashing, with script writing, with script testing, and with hardware. Write to join@freedomboxfoundation.org.
- The FunkFeuer Free Net network in Vienna/li>
You may also find it interesting to listen to a Scientific American podcast where attempts to build a hardier alternative internet are discussed.
Internet world image, courtesy of Shutterstock
Customer's Please Note: A Wireless Protection subscription is required for all Sophos Access Points
List Price:
Add to Cart to see sale price!
Overview:
The smarter way to simple, secure Wi-Fi
Sophos Wireless provides a simple, effective way to manage and secure your wireless networks. Managed from Sophos Central, it is easy to deploy as a standalone product or as part of your portfolio of cloud-managed solutions.
Highlights:
- Managed from Sophos Central
- One dashboard for an at-a-glance status
- Simple deployment and administration
- Increased visibility and control
- Secure guest access and hotspot setup
- Multi-site management and cloud scalability
Sophos Wireless managed from Sophos Central
With Sophos Wireless you can manage your wireless networks alongside other Sophos solutions or use our Sophos Central management platform solely for wireless network setup and control.
One dashboard for an at-a-glance status
The Sophos Wireless dashboard is your single pane of glass to get the status of your wireless networks, access points, connected clients and identify potential issues needing attention. Get all the key information at-a-glance in a concise manner and on a single screen.
Simple deployment and administration
Using the step-by-step guidance in our on-boarding wizard, creating networks, registering access points and adding sites is child’s play. Our solution is built to be simple to use - even for non-wireless experts - but that doesn’t mean you forfeit functionality. Schedule firmware upgrades to keep your network up-to-date and deploy new features.
Increased visibility and control
See which traffic is using your bandwidth to optimize the performance of your Wi-Fi and alert you to potential unwanted use of your resources. With Sophos Wireless you’ll know exactly what’s happening with your users and your wireless networks to avoid behavior which could put your security at risk.
Secure guest access and hotspot setup
Provide controlled internet access for visitors, contractors and other guests on your network. Using a daily password or time-based voucher, you can customize guest access with your own terms of service and branding. Use enterprise-grade backend authentication for a seamless user experience.
Multi-site management and cloud scalability
One of the benefits of a cloud-managed wireless solution is scalability. Whether you have just one growing network, or multiple sites, extending your Wi-Fi is as simple as adding an additional access point. With our basic site planning tools you get a first impression of what your set-up will look like, before doing a more detailed site survey and plan.
Features:
Plug & Play Deployment
Deploying Sophos Access Points is easy. Automatic setup and configuration means multiple wireless access points are up and running in minutes.
Simply plug the access point in and it automatically appears in the Sophos UTM user interface. Enable them from the console, and within seconds they become operational.
Reliable Mesh Networking
Sophos Access Points are ideal for creating multiple separate wireless zones. Configure a wireless network to provide employees access to internal network resources. On the same access point, you can offer wireless guests Internet access. Do it all without compromising the integrity of the internal network.
Access points include the dual-band, dual-radio AP 50, that can act as a repeater or bridge to extend Wi-Fi coverage to hard to wire areas.

Easy Guest Access
Set up guest hotspots for visitors or BYOD devices to control access to company resources. You get secure, easy-to-manage guest access out-of-the-box—without extra appliances, licenses or complex configuration.
- Fully customizable login pages and vouchers based upon templates—so you design the user experience and promote your company brand
- Automated mobile-device hotspot registration and authentication via SMS
- Set bandwidth limits and enforce inappropriate content filtering
Strong Encryption
Sophos UTM supports the strongest encryption and authentication standards available. Simply use your existing backend authentication, such as Active Directory, to allow quick and easy access for your employees. Know your wireless connections are completely secure.
- WPA2-Enterprise in combination with IEEE 802.1X (RADIUS authentication)
- Block-based encryption, providing the highest level of assurance that data is protected
- Sophos UTM monitoring easily detects failed authentication attempts
Optimized Performance
You get the ultimate in wireless performance with Sophos UTM and our Wireless Access Points.
- Support for the latest high-speed wireless standards including 802.11ac and 802.11n for up to Gigabit wireless speeds
- Automated channel selection and optimization for maximum performance and minimum interference under any situation
Complete UTM Security
Sophos Access Points send wireless traffic to the Sophos UTM appliance, where all security applications run.
- Wireless users get the same level of security as if they were connected physically to the LAN
- Add additional UTM protection modules to take full control of your network including network applications, quality-of-service, web surfing and more
Simple Management
At Sophos, simplicity is our mantra. You’ll have complete control over all the security features you need all in one place, with none of the complexity.
Sophos Mesh Network
We've invested heavily in streamlining our interface. This way you won't have to reach for the manual every time you need to update a policy or change a setting. So you're never more than a couple clicks from completing your task.
Complete on-box reporting
Our built-in reporting means you’ll know exactly what's happening with your users. Fix problems fast and shape your policies, keeping your users secure while boosting network performance. And, you get detailed reports as standard, stored locally with no separate tools required.
At-a-glance flow graphs show usage trends with predefined and customizable reports, providing key web activity. Report anonymization hides user names, requiring the four-eyes-principle to unhide them.
Flexible deployment
Sophos Network Agent
Sophos UTM gives you complete security—from the network firewall to endpoint antivirus—in a single modular appliance.
- Install as hardware, software or a virtual appliance or even in the cloud
- License our protection modules individually. Or, you can choose one of our pre-packaged licenses
- Centrally manage multiple appliances through IPsec VPN tunnels with our Free UTM Manager
Specifications:
Sophos APs are built on the latest enterprise-class, high-speed wireless chipsets with custom designed antennas, added CPU and memory resources, and hardware accelerated encryption.
| AP 15 | AP 30 | AP 50 | |
|---|---|---|---|
| Capacity | |||
| SOHO | Ceiling mounted, for larger offices | Dual-band/dual-radio, high-density WLAN environments | |
| Maximum throughput | 300 Mbps | 300 Mbps | 300 Mbps |
| Multiple SSIDs | 8 | 8 | 8 per radio (16 in total) |
| Technical Specification | |||
| LAN interface | 1 x 10/100/1000 Base TX | 1 x 10/100 Base TX | 1 x 10/100/1000 Base TX |
| Supported WLAN Standards | 802.11 b/g/n 2.4 GHz | 802.11 b/g/n 2.4 GHz | 802.11 a/b/g/n 2.4 and 5 GHz |
| DFS/TPC | - | - | - |
| Power over Ethernet (PoE) | 802.3af (PoE) | 802.3af (PoE) | 802.3at (PoE+) |
| Number of antennas | 2 external | 2 internal | 2 external |
| Number of radios | 1 | 1 | 2 |
| MIMO capabilities | 2x2:2 | 2x2:2 | 2x2:2 |
| Power supply | 90-240V, 50/60Hz | 90-240V, 50/60Hz | 100-240V, 50/60Hz |
| Power consumption (max.) | 2.5W | 8W | 9.6W |
| Physical Specifications | |||
| Dimensions (WxHxD) | 194 x 32 x 115 mm | 120 x 50 x 120 mm | 217 x 28 x 139 mm |
| Weight | 260g | 230g | 390g |
| Mounting options | Desktop/wall | Ceiling | Desktop/wall |
| Regulatory Compliance | FCC, CE, SRRC | FCC, CE, MIC, VCCI, NCC | FCC, CE, MIC, VCCI, NCC |
| AP 55 | AP 55C | |
|---|---|---|
| Capacity | ||
| Enterprise dual-band/dual-radio | Enterprise dual-band/dual-radio ceiling mount | |
| Maximum throughput | 867 Mbps + 300 Mbps | 867 Mbps + 300 Mbps |
| Multiple SSIDs | 8 per radio (16 in total) | 8 per radio (16 in total) |
| Technical Specification | ||
| LAN interface | 1 x 10/100/1000 Base TX | 1 x 10/100/1000 Base TX |
| Supported WLAN Standards | 802.11 a/b/g/n/ac 2.4 GHz and 5 GHz | 802.11 a/b/g/n/ac 2.4 GHz and 5 GHz |
| DFS/TPC | Yes | Yes |
| Power over Ethernet (PoE) | 802.3at (PoE+) | 802.3at (PoE+) |
| Number of antennas | 2 external | 4 internal |
| Number of radios | 2 | 2 |
| MIMO capabilities | 2x2:2 | 2x2:2 |
| Power supply | 100-240V, 50/60Hz | 100-240V, 50/60Hz |
| Power consumption (max.) | 11W | 13W |
| Physical Specifications | ||
| Dimensions | 183 (W) x 36 (H) x 183 (D) mm | 200 (Diameter) x 37 mm (Height) |
| Weight | 500g | 640g |
| Mounting options | Desktop/wall | Ceiling |
| Regulatory Compliance | FCC, CE | FCC, CE, UL (plenum-rated) |
| AP 100 | AP 100X | AP 100C | |
|---|---|---|---|
| Capacity | |||
| Enterprise dual-band/dual-radio | IP67 Enterprise outdoor/exterior wall-mount | Enterprise-grade ceiling mount | |
| Maximum throughput | 1.3 Gbps + 450 Mbps | 1.3 Gbps + 450 Mbps | 1.3 Gbps + 450 Mbps |
| Multiple SSIDs | 8 per radio (16 in total) | 8 per radio (16 in total) | 8 per radio (16 in total) |
| Technical Specification | |||
| LAN interface | 1 x 10/100/1000 Base TX | 1 x 10/100/1000 Base TX | 1 x 10/100/1000 Base TX |
| Supported WLAN Standards | 802.11 a/b/g/n/ac 2.4 and 5 GHz | 802.11 a/b/g/n/ac 2.4 and 5 GHz | 802.11 a/b/g/n/ac 2.4 and 5 GHz |
| DFS/TPC | Yes | Yes | Yes |
| Power over Ethernet (PoE) | 802.3at (PoE+) | 802.3at (PoE+) | 802.3at (PoE+) |
| Number of antennas | 3 external | 6 external | 6 internal |
| Number of radios | 2 | 2 | 2 |
| MIMO capabilities | 3x3:3 | 3x3:3 | 3x3:3 |
| Power supply | 100-240V, 50/60Hz | 100-240V, 50/60Hz | 100-240V, 50/60Hz |
| Power consumption (max.) | 13W | 15W | 13W |
| Physical Specifications | |||
| Dimensions (WxHxD) | 183 (W) x 36 (H) x 183 (D) mm | 255 (W) x 225 (H) x 90 (D) mm | 200 (Diameter) x 37 (Height) mm |
| Weight | 505g | 2.5 kg | 640 g |
| Mounting options | Desktop/wall | Wall/pole | Ceiling/desktop |
| Regulatory Compliance | |||
| Certifications | FCC, CE | FCC, CE, UL | FCC, CE, NCC, UL (plenum-rated) |
| Wireless Controller | UTM 100 | UTM 110 | UTM 120 | UTM 220 | UTM 320 | UTM 425 | UTM 525 | UTM 625 |
|---|---|---|---|---|---|---|---|---|
| Recommended Sizing | ||||||||
| Number of Access Points | 1 | 2 | 4 | 8 | 16 | 32 | 64 | 128 |
| Number of Wireless Users | 5 | 10 | 25 | 50 | 100 | 250 | 500 | 1000 |
Documentation:
Download the Sophos UTM Wireless Data Sheet (PDF).
Pricing Notes:
- Customer's Please Note: A Wireless Protection subscription is required for all Sophos Access Points
- Pricing and product availability subject to change without notice.
List Price:
Add to Cart to see sale price!
List Price:
Add to Cart to see sale price!
List Price:
Add to Cart to see sale price!
List Price:
Add to Cart to see sale price!
Sophos Network Protection
List Price:
Add to Cart to see sale price!
Sophos Sg Mesh Network
Sophos Xg Mesh Network
List Price:
Add to Cart to see sale price!
